AWS For Everyone - Part IV: Networking Services, VPC, CIDR, CloudFront and more!
This post is part of a series that are meant to prepare you for the AWS CCP exam. In this post, I discuss the networking services in AWS to ace the exam.
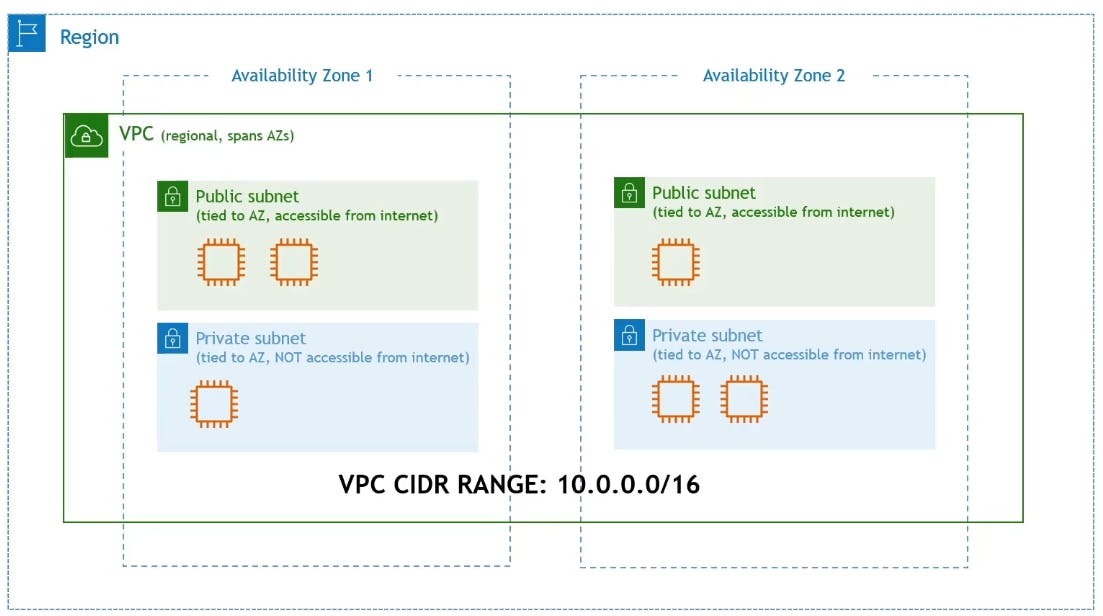
VPC (Virtual Private Cloud)
VPC is your own private network (cloud) within the cloud. It isolates your resources from everyone else's.
When you create an AWS account, you automatically have a default VPC and whenever you create an EC2 instance for example, it will be created in that VPC.
A VPC is an isolated cloud for yourself, but you can expose it or part of it to the internet through the internet gateway. You can create a subnet inside the VPC. If the subnet is exposed to the internet through routes, it's called a public subnet. While if it wasn't, it's called a private subnet. Inside the subnets is where our resources live (EC2 instances, databases, etc).
Classless Inter-Domain Routing (CIDR)
Notation for describing blocks of IP addresses.
Each resource inside the subnet has a private IP address which comes from the CIDR that is defined at the VPC level. The CIDR range defines how many IP addresses, and thus how many resources, we can have inside our VPC.
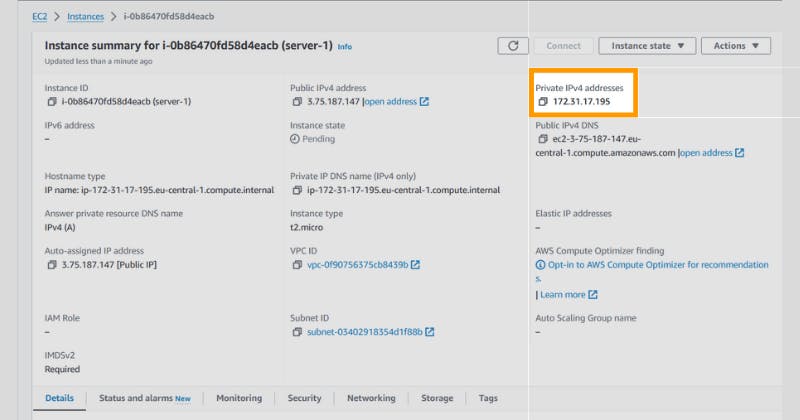
And if you go to the VPC panel, you'll see your VPC's IP CIDR range:
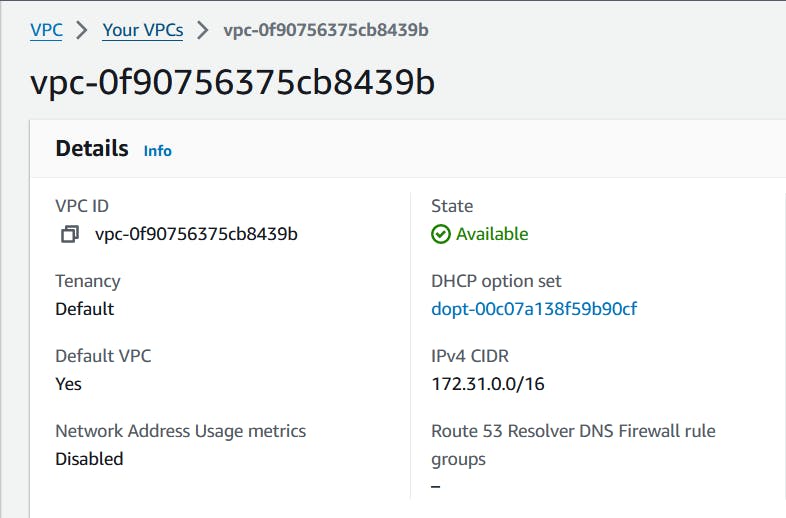
If you compare the two number, in my case 172.31.0.0/16 for the CIDR range and 172.31.17.195 for the EC2 instance's private IP address.
For the CCP exam, you're not expected to be an expert in IP addresses, but if you go to this website: https://cidr.xyz/ and insert 172.31.0.0/16 inside, you'll see that the number of possible IP addresses that can be derived from this range CIDR range is 65,536 unique IP addresses which also means 65,536 different resources within a single VPC.
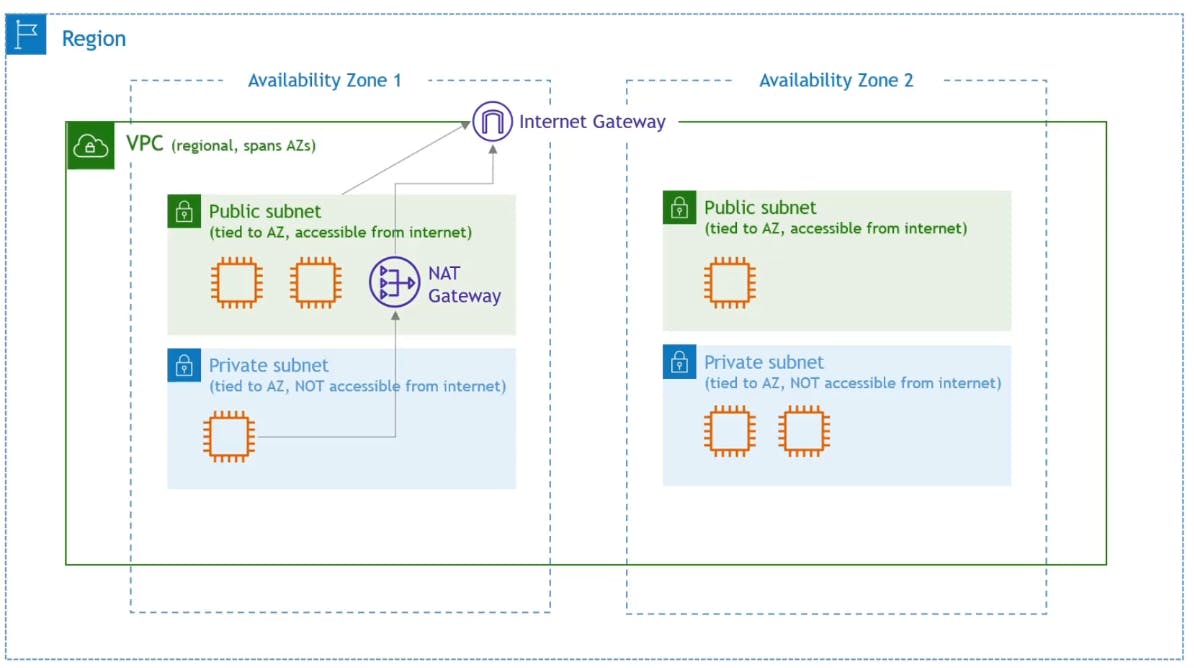
NAT Gateway
We discussed previously that private subnets don't have routes that get access in and out for the internet. But what if you want to connect to the internet inside a private subnet to do patching or install some application? In this case you create a NAT Gateway inside a public subnet, and access it from the private subnet which is eventually connects to the internet.
VPC Endpoints
VPC Endpoint is just a private network within AWS that allows access to AWS services without going to the public internet.
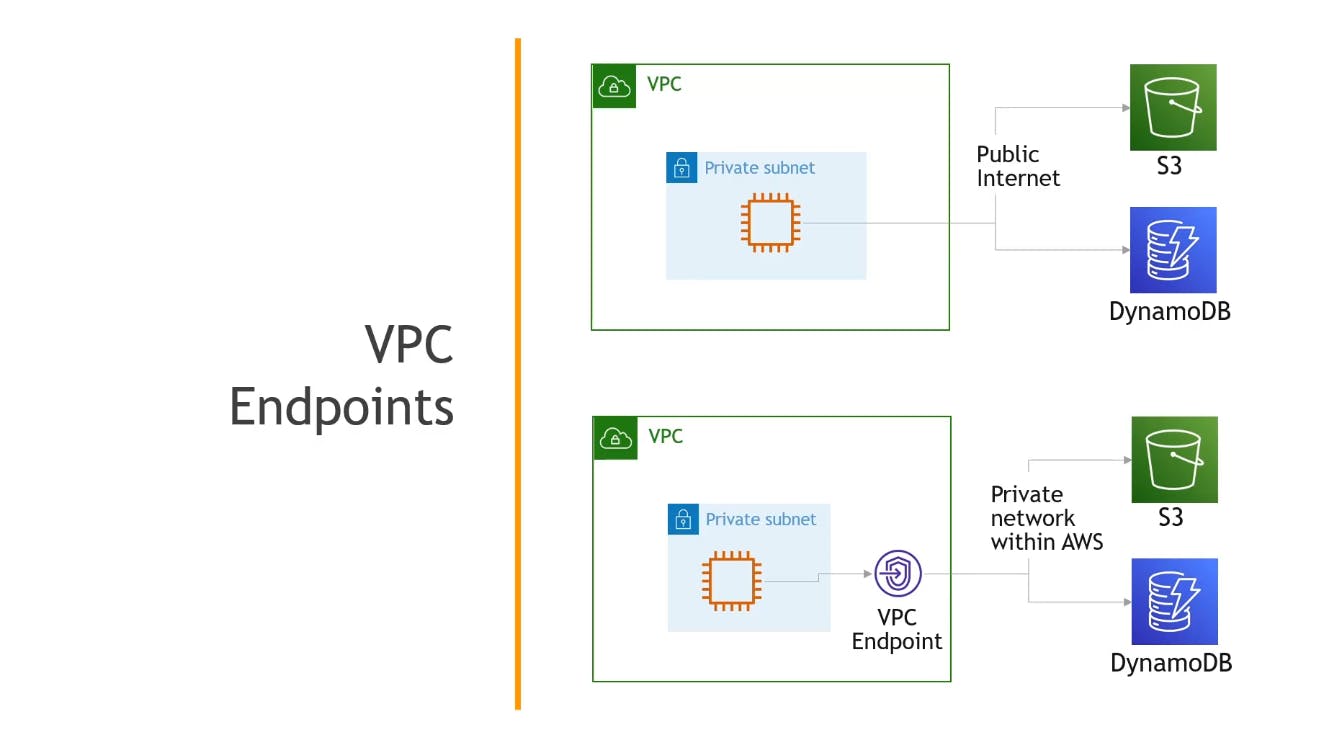
There are 2 types of VPC endpoints:
Gateway Endpoints: allow access to S3 and DynamoDB only.
Interface Endpoints: allow access to all other services.
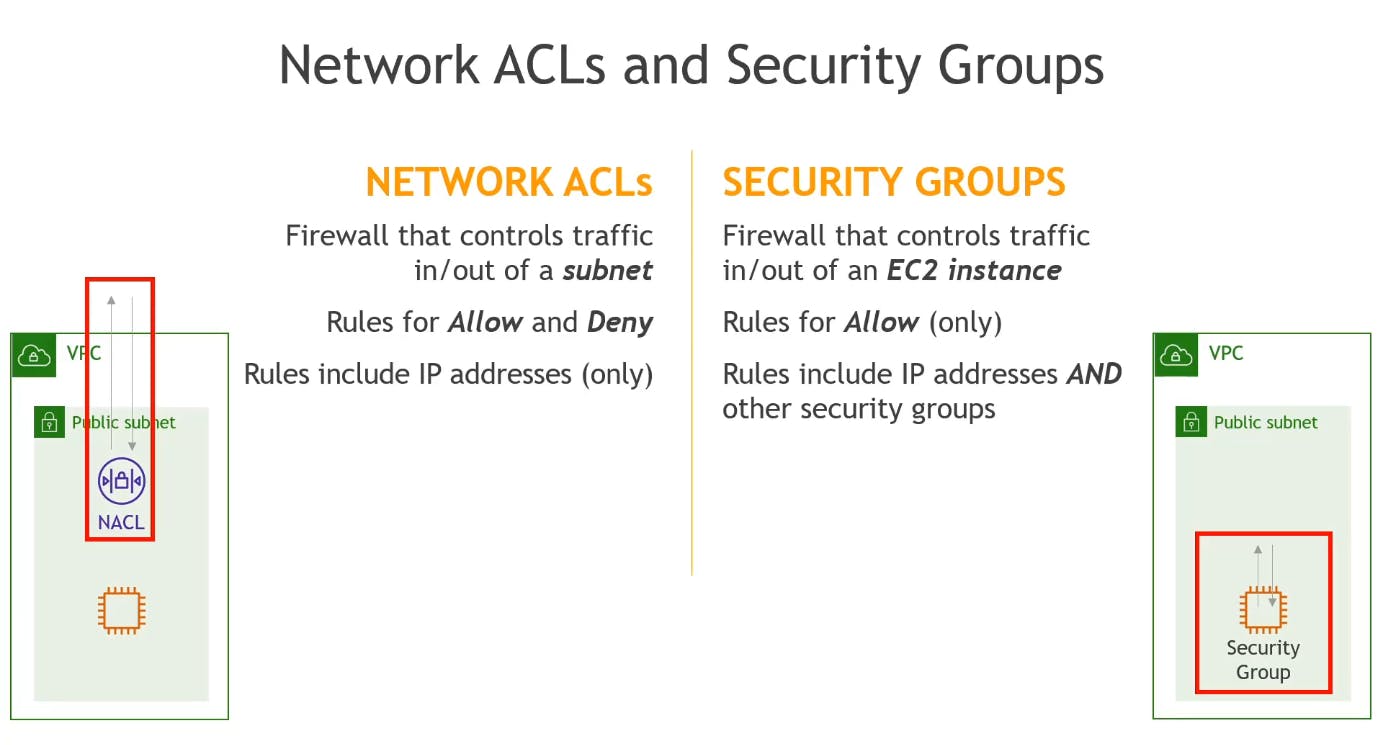
Network ACLs and Security Groups
For the exam, remember that securing subnets is feasible by Network ACLs (Access Control Lists) while securing EC2 instances is feasible through Security Groups like in the diagram below:
VPC Flow Logs
Flow Logs are useful to log all traffic on the VPC network.
VPC Peering
VPC Peering means that multiple VPCs can be peered together so they behave as one.
VPCs can't have overlapping CIDR ranges. Also it is not transitive, which means that each VPC must directly connect to the other.
CloudFront
A Content Delivery Network (CDN). It is a geographically distributed network that delivers content to users faster by caching.
It is used usually to cache media files like images and videos. When the browser request the video, CloudFront first looks at its cache, if there is that video, the video is served from CloudFront. If it doesn't, it fetches the video and caches it.
AWS Global Accelerator
It is a service to increase availability but not caching like CloudFront, but by doing network routing of traffic, moving off the public internet.
Route 53
It's a DNS service where you can purchase domains, DN routing, health checking.
Direct Connect and Site-to-Site VPN
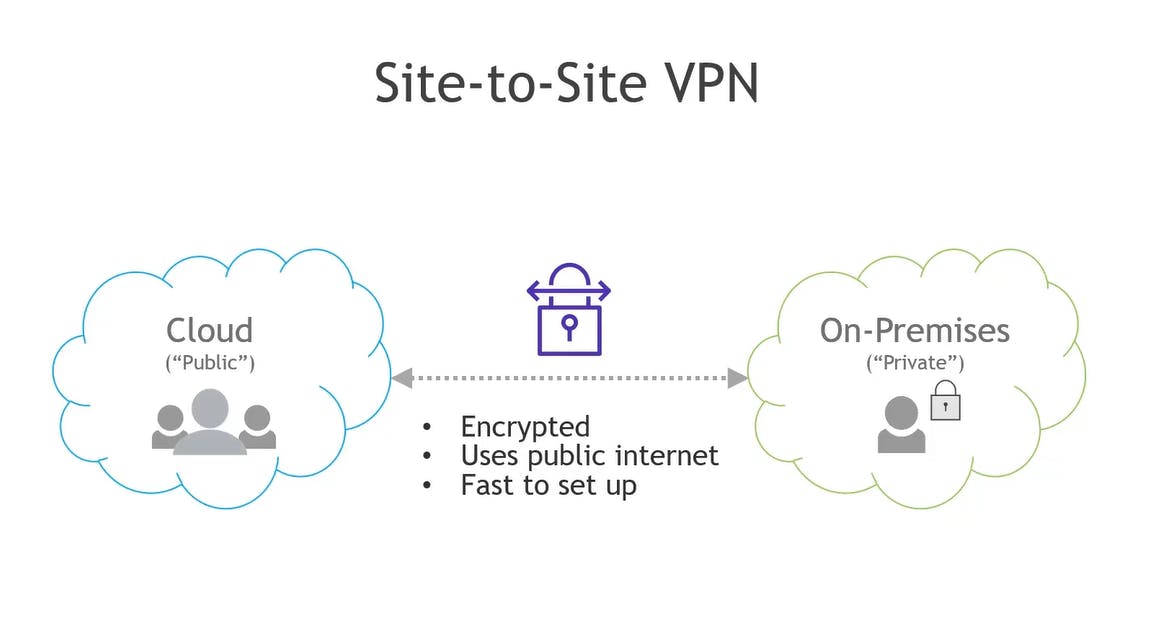
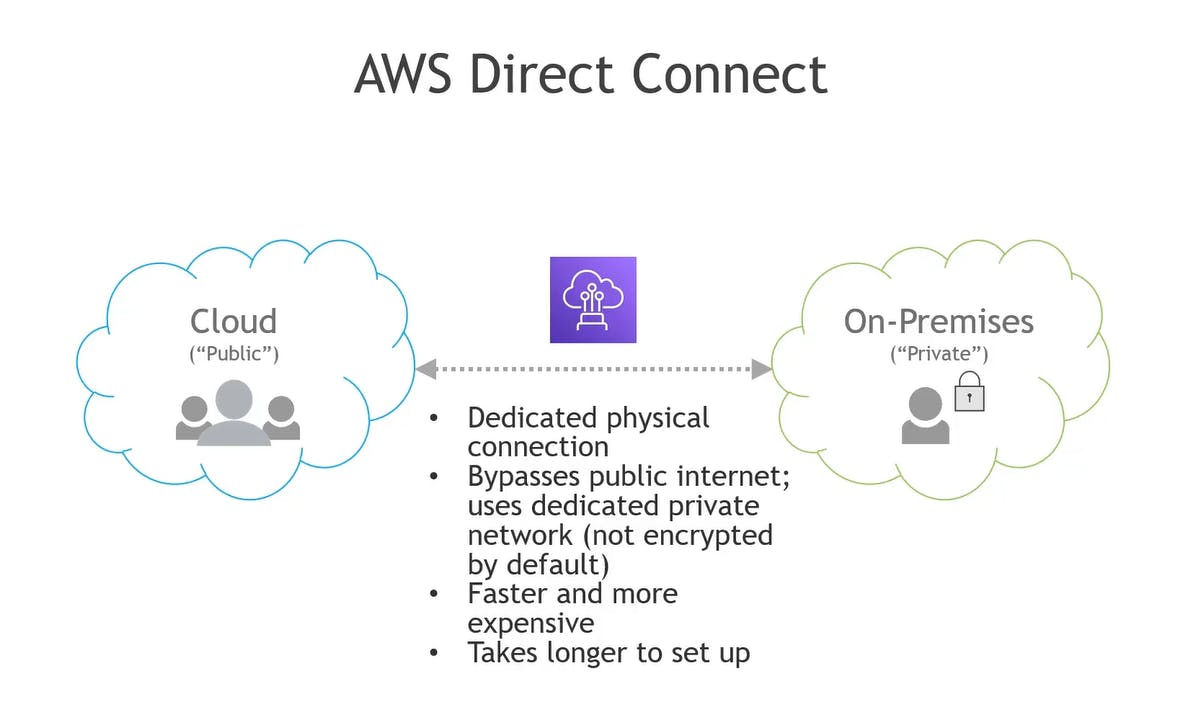
I hope you enjoyed this overview of the networking services of AWS. If you want to look at the previous posts of this series, please check out my blog here.
You might also be interested in looking at my YouTube channel here where I make tutorials on how to build web applications from code production: