AWS Shield
AWS Shied protects against DDoS attacks. What is DDoS?
DDoS
Distributed Denial of Service is when a legitimate user is denied from accessing the server because a hacker is using thousands of computers (bots or zombified computers) to perform a lot of requests to the same server in a very short period of time that makes the server overwhelmed and goes down which causes denial of service to legitimate users like in the diagram below:
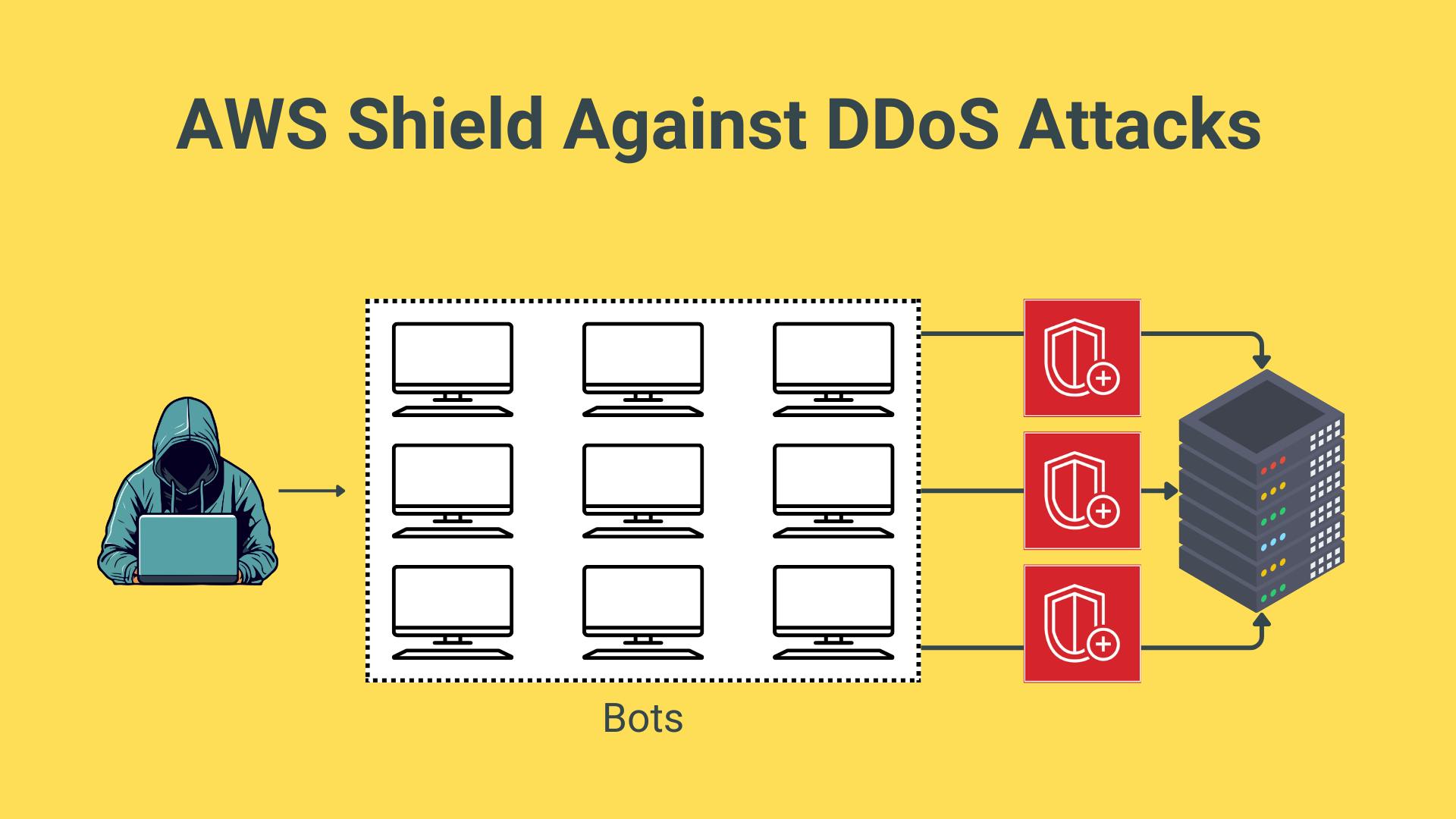
AWS protects our servers using the AWS Shield (the red logo).
AWS Shield has two versions: standard and advanced. The standard is applied by default and it protects all customers from the most common DDoS attacks and it's free. The advanced version is paid and protects against sophisticated attacks and integrates with other services like CloudFront and Elastic Load Balancing and comes with AWS Web Application Firewall (WAF) at no extra cost.
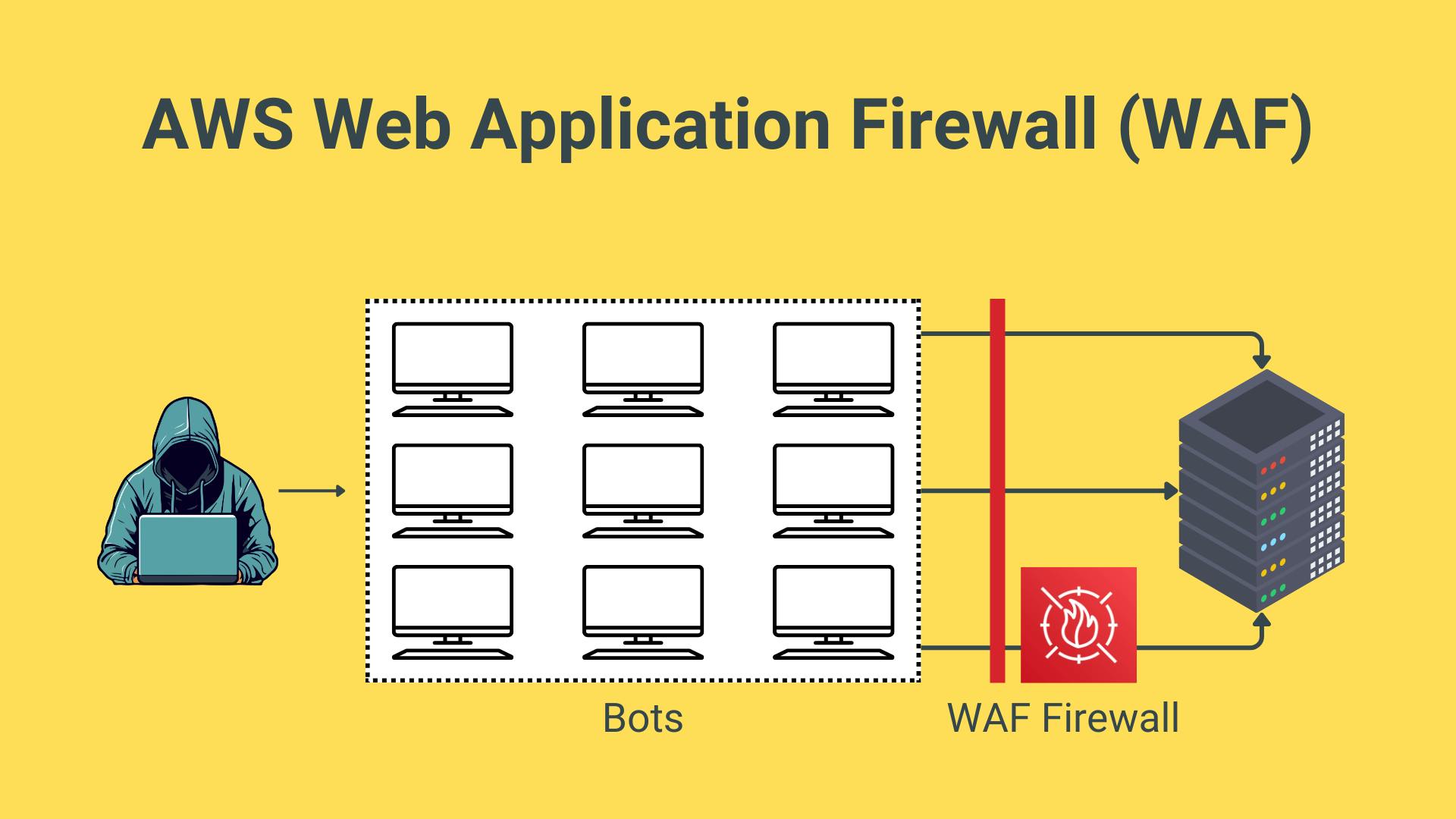
AWS Web Application Firewall (WAF)
A firewall can be configured with rules to control incoming and outcoming traffic for applications. Example:
Allow, block count the number of requests coming to your server from a certain location.
Block IP addresses coming from a certain country.
Block certain IP addresses.
Only 100 requests can be made to the server every 5 minutes.
AWS Key Management System (KMS)
This is the primary service for encryption in AWS. AWS manages the hardware, software and the keys for you. It is also integrate with other services like S3 buckets, EBS, Redshift, Secret Manager and CloudTrail.
The FIPS 140-2 Compliance (security level) of KMS is level 2.
Types of keys:
AWS Managed Keys: AWS creates and manages those keys and they are used by AWS services and have the "aws" prefix. Examples:
aws/lambda
aws/cloud9
aws/s3
Customer Managed Keys: you create the keys and make policies on who can create or rotate the keys.
Custom Key Stores: They are created by AWS CloudHMS and you own and manage those yourself.
AWS CloudHMS (Hardware Security Module)
AWS provisions the hardware and you do everything else. That means AWS cannot access or recover your keys. It has limited integration with other services but it is considered of level 3 in FIPS 140-2 Compliance.
AWS Certificate Manager
This service provisions, manages and deploys public and private SSL/TLS certificates. Public certificates are free and used for the public internet. Private ones are for private networks.
Certificates
Certificates are text files put on your server to identify yourself as a reputable to ensure encrypted communication between the server and the client. They use SSL/TLS protocols.
Certificates can be loaded on AWS services like API Gateway, Elastic Load Balancer and CloudFront distributions. Thos services accept requests from the outside world to your servers.
AWS Secrets Manager
Let's suppose you have an application that uses username and password to access your database and retrieve and store data on it. How would you go in storing those sensitive credentials? Of course not hard-coding them. AWS has a service for this called AWS Secrets Manager to protect the secrets needed by your applications and services.
Amazon Macie
Macie is a service responsible for PIIs (Personally Identifiable Inofrmation).
It works with the S3 storage service and it automatically takes inventories of the S3 buckets and then identifies and analyzes the PII data using Machine Learning and pattern matching, and then takes the output and use it to automate workflows and remediate the issues by integrating with CloudWatch events and EventBridge.
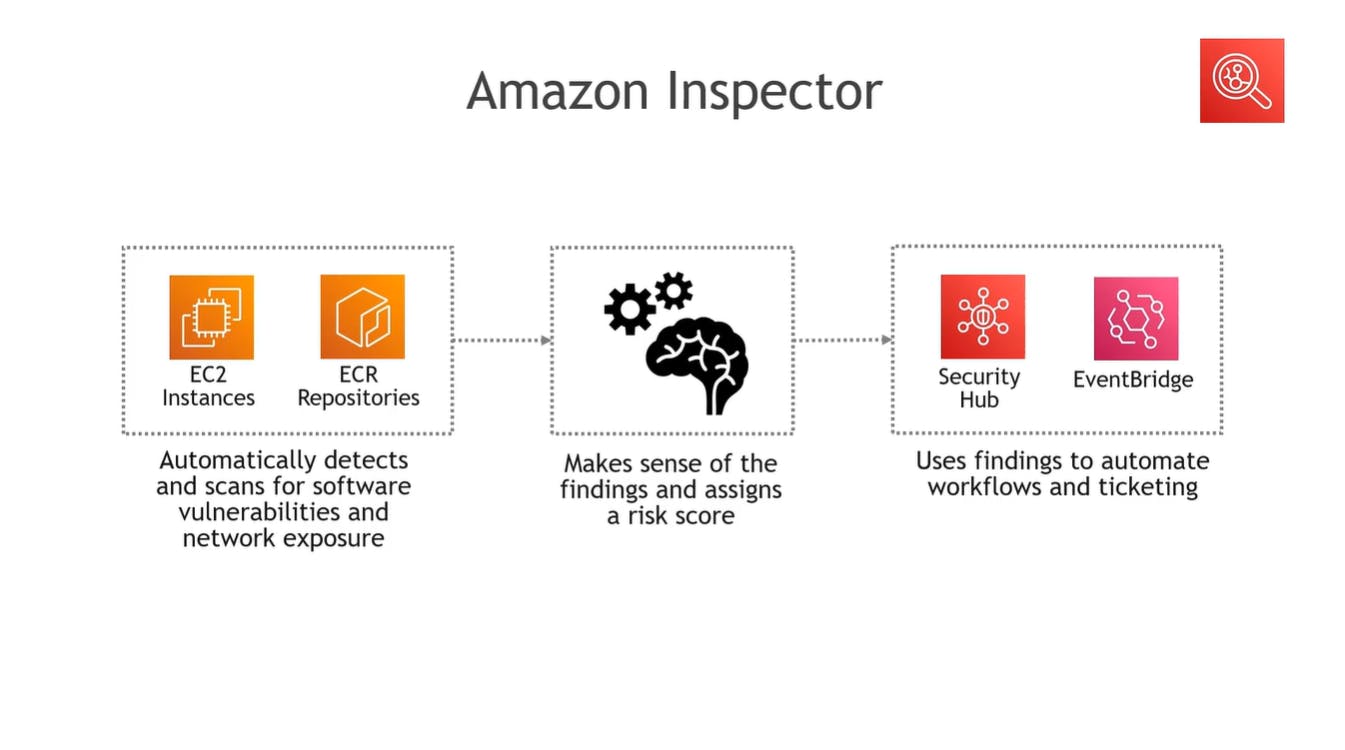
Amazon Inspector
It detects vulnerability issues in EC2 instances and ECR repositories for software vulnerabilities and network exposure and assigns problem tickets to the server owner to solve the problem.
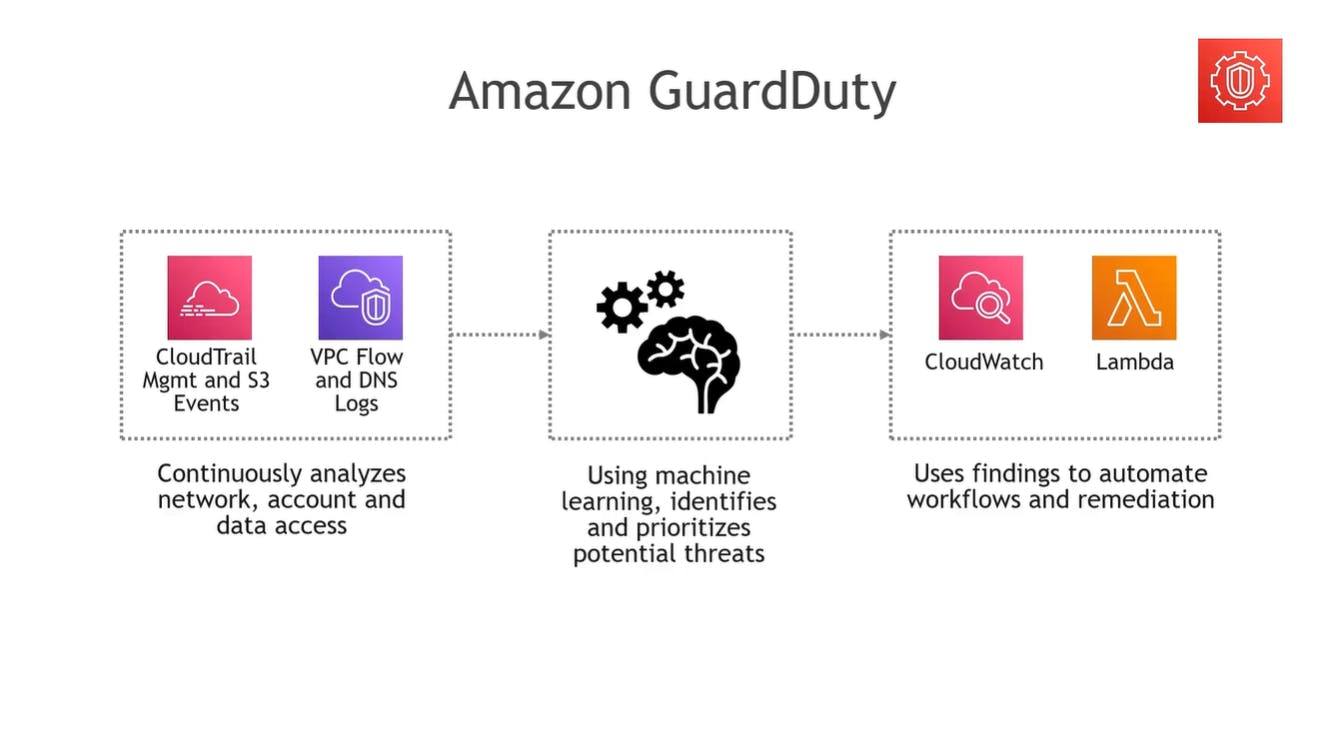
Amazon GuardDuty
It automatically looks at CloudWatch Management events and S3 events, as well as the flow and DNS logs from your Virtual Private Cloud (your private network) and analyze it and automate workflows to address the issues.
It's very similar to Amazon Inspector, but GuardDuty watches the entire AWS account, while the Inspector is specialized only in applications.
AWS Config
It takes an inventory and records and audit the configuration changes of your AWS resources. So you define what happens when a rule is matched. E.g:
Takes the inventory of all your S3 buckets and receive an alert when one of them becomes publicly accessible (rule).
Receive an alert when an unauthorized port is open on one of the security groups (rule).
AWS Security Hub
It pulls everything together into a consolidated place where you can view and audit security isses.
It requires AWS Config to be enabled.
It works across multiple accounts.
- Aggregates data from Inspector, Macie, Firewall Manager, Systems manager.
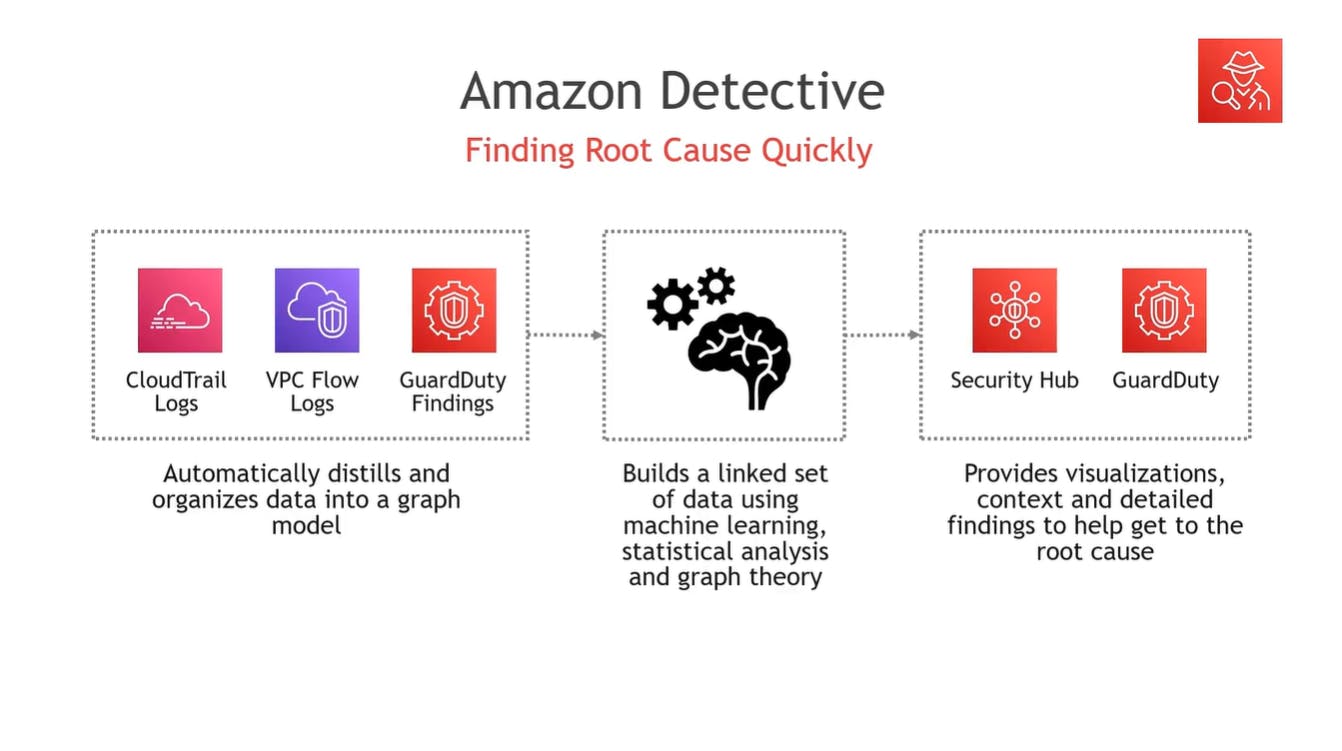
Amazon Detective
Finds the root cause of security issues.
Amazon Artifact
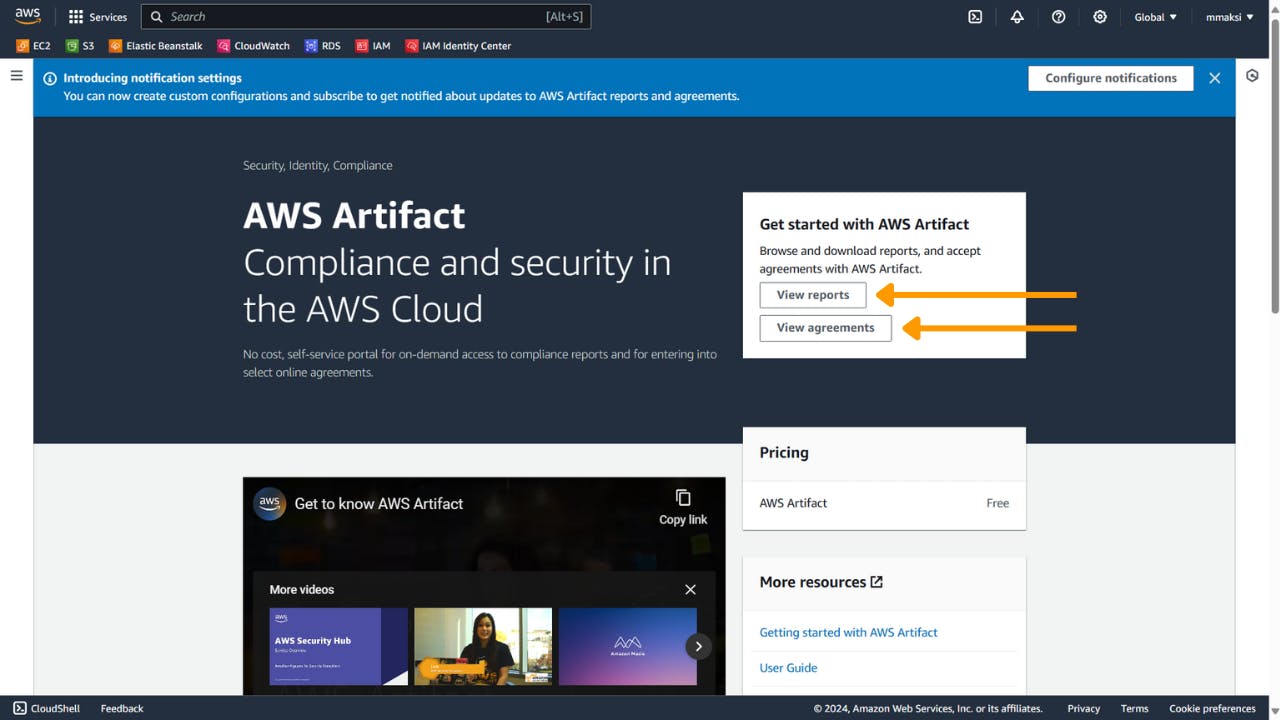
It's a free self-service portal to access AWS's internal compliance reports and agreements so that your business is compliant with the regulations set by the country or the industry or the services like payment services. Download the Artifact reports and give them to the auditors and say yes we're using AWS which shows compliant with XYZ services you're using.
To see and download those reports, go to reports and agreements as shown below and look for the compliance report you're looking for and download it.
E.g: look for Payment Card Industry (PCI) compliance report.
I hope you enjoyed this broad overview! You might also love to look at my YouTube content here:
