In the sprawling digital ecosystems of today's enterprises, security stands as the paramount concern, especially when navigating the complex cloud environments. Amazon Web Services (AWS), a leader in cloud computing, offers a robust solution to this ever-present challenge through its Identity and Access Management (IAM) service. AWS IAM embodies the frontline defense of AWS security, enabling full control over who can access and interact with resources in your AWS environment. This powerful service is not just about keeping unauthorized users out; it's about finely tuning the access and permissions for those within an organization, ensuring that the right individuals have the right access to the right resources, at the right times, for the right reasons.
AWS provides a lot services, and in this article you will learn about the IAM service, and I will guide you step by step on how to create users, user groups, attach permissions and policies so you have full control over your AWS Dashboard or what is known as AWS Management Console, and finally I will discuss few best practices to secure your AWS Management Console.
Identity and Access Management (IAM)
IAM is a service to securely control access to your AWS resources. It controls authentication and authorization.
We have Users, User Groups, Roles, Policies inside the IAM to control authentication and authorization to your AWS environment.
Let's start discussing Users, User Groups, Roles and Policies inside the IAM service.
1. IAM Users
Let's understand the difference between Root User and IAM User.
Every AWS account has a single Root User. It has unrestricted access and there are tasks that only the Root User can do, which are:
Close AWS account
Change AWS Support Plan
Change AWS account settings
While IAM users are accounts created by the Root User and we can have as many as we want and we can assign different privileges to each IAM account. It's easy to close IAM accounts or restrict access or change their privileges.
Best Practices:
Always work in IAM account, not Root to follow the principle of least privileges.
Don't create access keys for the root user.
Delete the access keys for the root user if you have them.
Enable MFA.
Let's setup 3 IAM users: John Smith, William Smith, and Mark Maksi (me).
Go to the IAM Dashboard and click on Users on the left hand side:
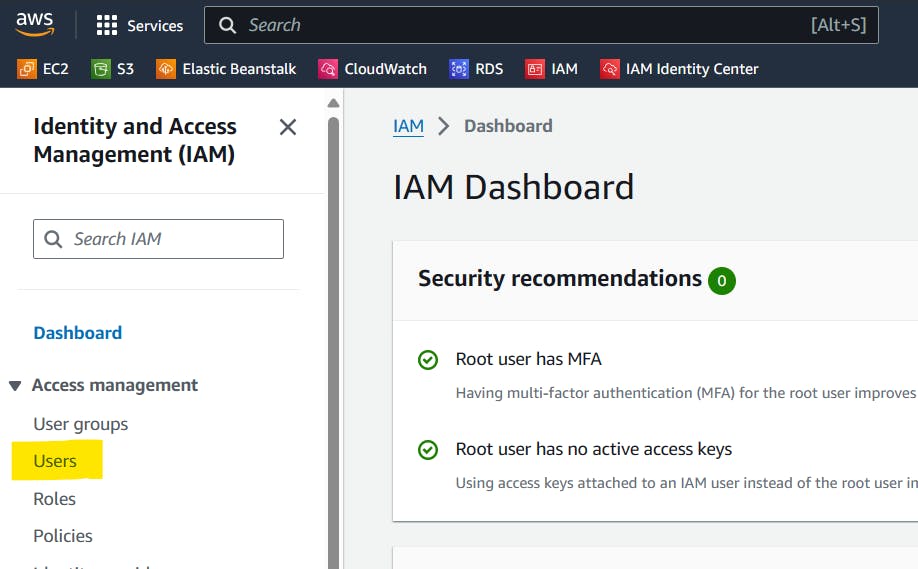
After that follow those steps which are straight-forward.

In the next step you'll be prompted to add the user to a group, you don't have groups at this moment so we can skip it and create groups later.
In the final step, you'll see the Console sign-in URL which is the URL that John Smith must use to login with the username and password. You must store those credentials or email them to John Smith.
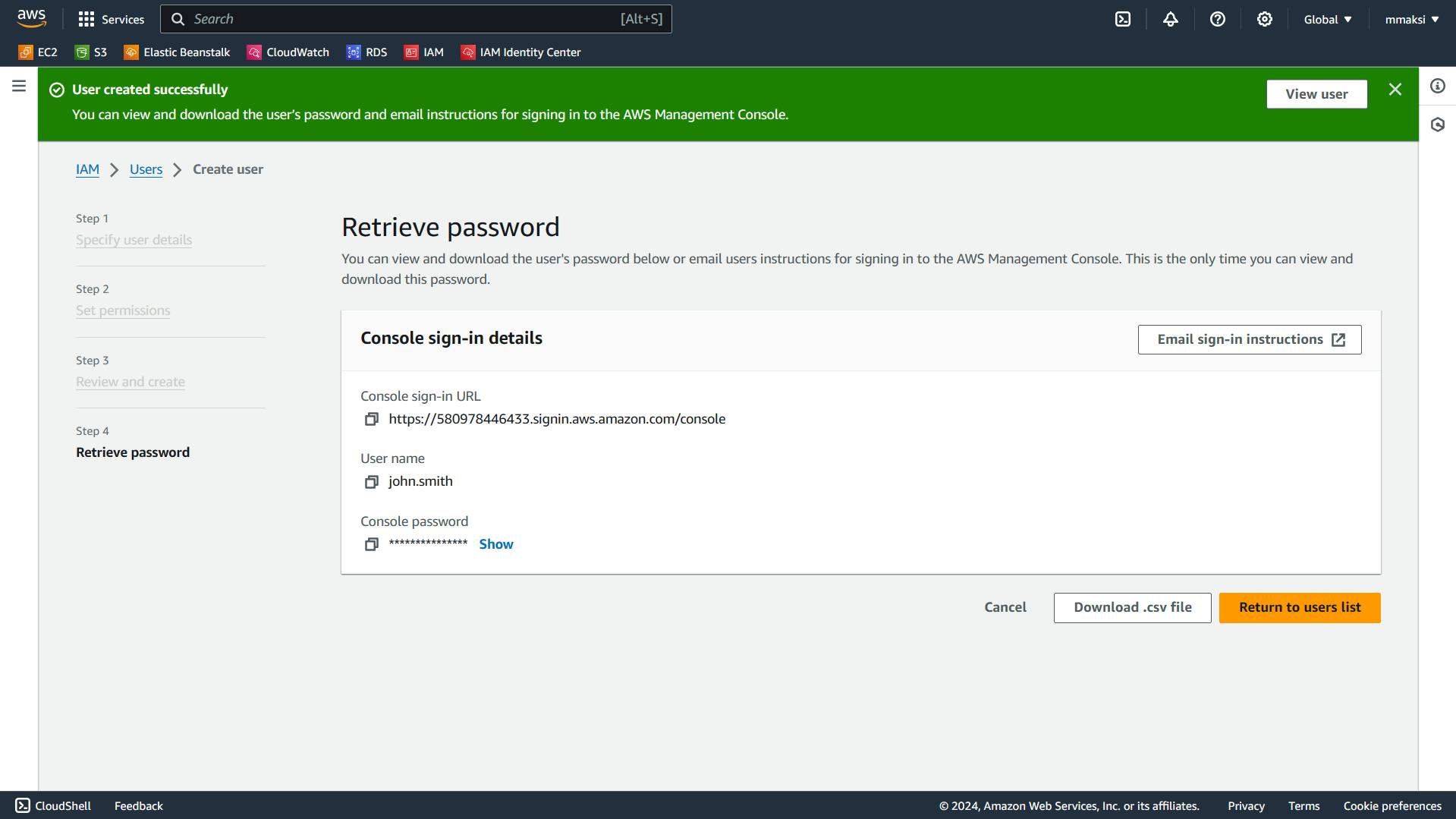
Repeat the steps for Mark Maksi and William Smith.
2. IAM User Groups
Groups are a collection of users. We create groups so that we can assign privileges to the group and any user that joins any group will inherit the privileges of the group.
Create "Admins" group and add William Smith to it.
Create "Developers" group and add John Smith to it.
Create Testers" group and add Mark Maksi to it.
3. IAM Roles
Roles are permissions given to one service to interact with another service. When a user or a group of users is give the role of "administration" with certain permissions, they can perform all the tasks that require those permissions. Whatever role you have, that's what you can do.
4. IAM Policies
Policy = who can do what to what resources.
Example: allow Admin group to rotate their own credentials programmatically and in the console.
Let's add a policy (permissions) to the Testers group we added previously that allows anyone in the Testers group to have full access to the S3 service.
Go to User Groups. Click on the Testers group. Click on the permissions tab, and click on "Attach policies"

And search in the built-in policies for "s3". I chose the easiest one which is full access to the S3 service as shown below.

Best Practices
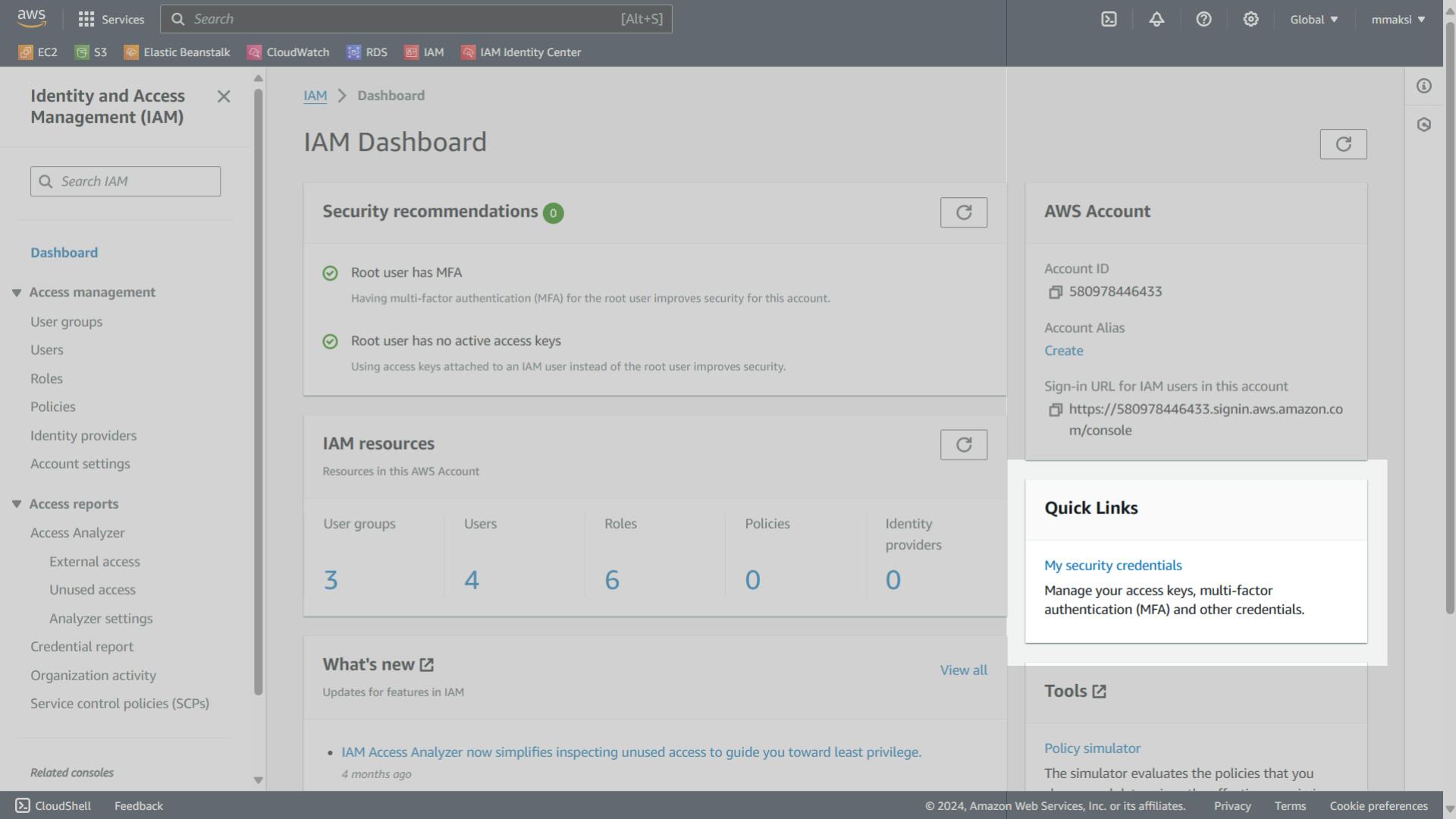
- Enable the MFA from the Quick Links in the IAM service. It's best to add it to all users including Root and IAM users.
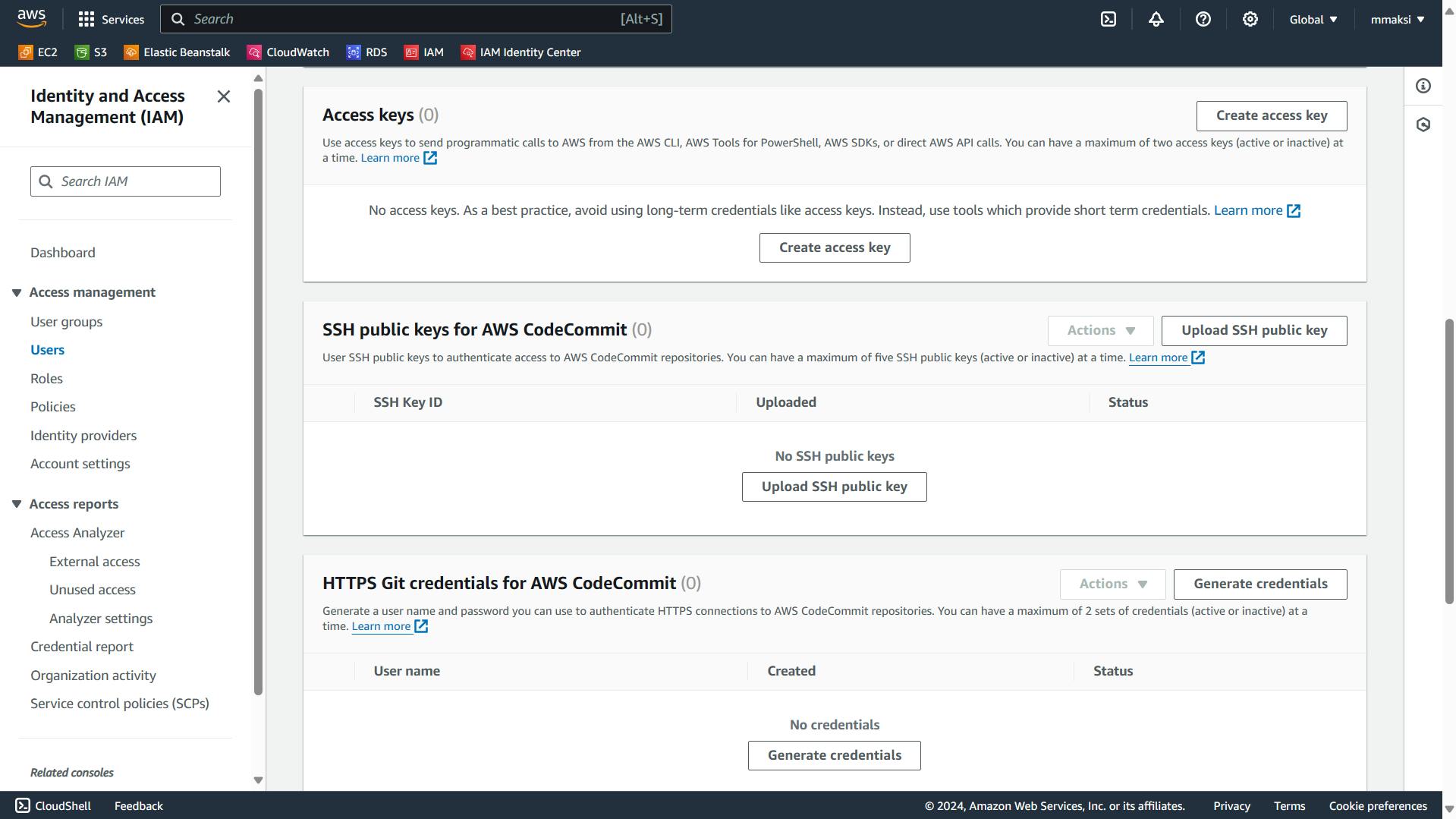
- Create access keys to IAM users but remove them for the Root user.
Access keys are like API keys, they allow you to access AWS services programmatically using the CLI. To add or remove access keys go to a specific user, in my case John Smith, and click on create access key as shown below:
- Password policies
Sign in as a Root user and go to Account settings in the IAM service as shown below to create or edit your own password policies to control how IAM users should enter their passwords.

That's it! I hope you found this tutorial helpful. If you're interested in learning software development from code to production, feel free to check out my growing YouTube channel here: https://www.youtube.com/@markmaksi
